How does search engine
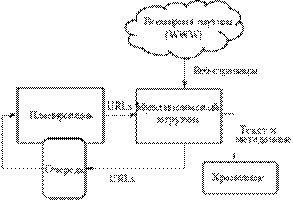
Figure 24- job of search engine
High-level architecture of the standard crawler
Main components of a search engine crawler, indexer, search engine:.
As a rule, the system works in stages. First, the crawler receives the content, then the indexer generates a searchable index, and finally, the search engine provides the functionality to search for the indexed data. To update the search engine indexing of the loop is executed again.
Search engines work by storing information about many web pages, which they receive from HTML pages. Crawler or "crawler"(eng. -Crawler)a program that automatically runs through all the links found on the page, and makes them stand out. Crawler based on references or on the basis of a predetermined list of addresses, searches for new documents, not yet well-known search engine. The site owner can exclude certain page using a robots.txt, using which you can prevent the indexing of files, pages or the site directory.
Searcher operates to output files received from the indexer. The search engine receives user requests, processes them using the index and returns search results
4.Safety issues in industrial information and communication technologies.
Vision of information security of the Republic of Kazakhstan
Information Security Concept of the Republic of (Hereinafter - the Concept) is designed to ensure that the interests of society and state in the information sphere.
recently updated issue of equal participation of the Republic of Kazakhstan in the international exchange of information and processes in the international regulation of information security. The need to defend the national interest requires an increase in the activity of state bodies in the framework of existing international organizations introduction.
Thus, the current state of information security is characterized by the following threats:
1) the imperfection of information security system and dysfunction of critical facilities information;
2) low level of production, the and the use of modern information and communication technology that does not meet the objective needs of and
society,
3) depending on the Republic of Kazakhstan on import of information technologies, informatization and protection of information, the use of which may cause damage to the national interests of the country;
4) the rise of information warfare between the world's leading centers of power, preparation and conduct of foreign states struggle in the information space;
5) non-constructive policy of foreign countries in the field of global information monitoring, dissemination of information and the new information technologies;
6) the development of information manipulation technologies;
7) the possibility of destructive information impact on the public consciousness and public institutions, the applicator damage to the country's national interests;
8) dissemination of false or deliberately distorted information that could harm the national interests of the Republic of Kazakhstan;
9) openness and vulnerability of the national information space from external influence;
10) lack of effectiveness of information support of public policies;
11) a weak protection and low competitiveness national information space;
12) non-compliance of national content quality of the objective requirements of Kazakhstan's society and world level;
13) increase in crime, including transnational crime, as well as extremist and terrorist activities, using information and communication technologies;
14) attempts unauthorized access to information resources Republic of Kazakhstan, resulting in damage to its national interests;
15) activities of foreign intelligence and special services, as well as foreign political and economic structures, aimed against the interests of the Republic of Kazakhstan;
16) violations of secrecy when working with information constituting state secrets of the Republic of Kazakhstan, as well as willful misconduct and unintentional errors and irregularities in the handling of information of restricted access;
17) lack of legal regulation of information sphere system;
18) natural disasters and catastrophes;
19) unlawful actions of state structures, leading to a violation of the legitimate rights and interests of individuals and legal entities, the state in the field of information
Aims and objectives
The aim of the Concept is creation of a national information security system that guarantees the protection of the national interests of the Republic of Kazakhstan in the field of information
to achieve this goal it is necessary to solve the following set of tasks:
1) the development of information security management system that enables ensure security of the country's national information infrastructure, and a single national information space;
7) 2016, the level of maintenance to eliminate downtime of information systems for information security will be reduced to 20 minutes;
8) will be provided by the production of the domestic computer hardware, accessories, peripherals and software
9)increase the level of innovative activity of industrial enterprises;
10) legal framework governing the information sector will be improved, including through international cooperation;
11) will improve the system of staffing in the field of information security and the protection of state secrets.
Questions:
5. What is the software for the solution of tasks of the specialized professional sphere?
6. Safety issues in industrial information and communication technologies
7. What is the modern IT trends in the professional sphere?
8. What are the differences between using of search engines and electronic resources in the professional purposes?
References
1. June J. Parsons and Dan Oja, New Perspectives on Computer Concepts 16th Edition - Comprehensive, Thomson Course Technology, a division of Thomson Learning, Inc Cambridge, MA, COPYRIGHT © 2014.
2. Lorenzo Cantoni (University of Lugano, Switzerland) James A. Danowski (University of Illinois at Chicago, IL, USA) Communication and Technology, 576 pages.
3. Craig Van Slyke Information Communication Technologies: Concepts, Methodologies, Tools, and Applications (6 Volumes). ISBN13: 9781599049496, 2008, Pages: 4288
4. Utelbaeva A.K.,Utelbaeva A.K. Study guide for lectures on discipline “Computer science”, Shimkent 2008, 84 pages.
Дата добавления: 2017-05-18; просмотров: 2486;
